A Key Part of Fortra
Digital Defense is proud to be part of Fortra’s comprehensive cybersecurity portfolio. Fortra simplifies today’s complex cybersecurity landscape by bringing complementary products together to solve problems in innovative ways. These integrated, scalable solutions address the fast-changing challenges you face in safeguarding your organization. With the help of powerful tools from Digital Defense and others, Fortra is your relentless ally, here for you every step of the way throughout your cybersecurity journey.
Our SaaS platform:
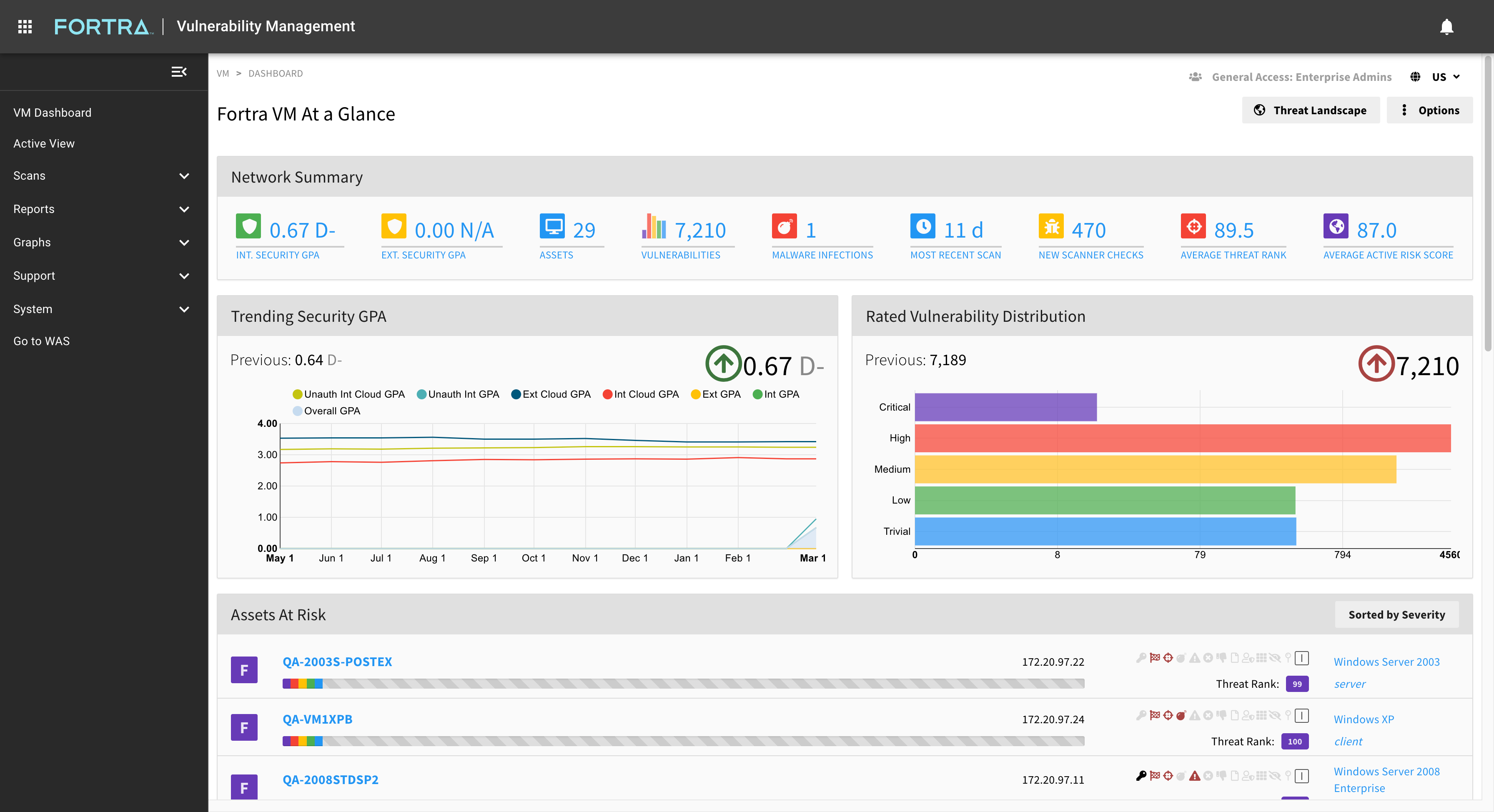
Digital Defense's best-in-class SaaS vulunerability management and threat assessment platform is cloud-native, easy to use, and committed to the highest level of performance and accuracy.
Create a customized vulnerability management program by layering the proactive security solutions available on the SaaS platform, including:
|
Accurate vulnerability management that's comprehensive and easy-to-use. |
|
|
Conductive dynamic testing on your web applications. |
|
|
Ethical hacking services that locate security weaknesses before they can be exploited. |
|
|
Assess active threats in your network, accurately and quickly. |
Professionally Customized Cybersecurity Solutions
Our certified experts evaluate each customers' unique needs and make recommendations for products and services that go beyond standard security subscriptions. In addition to our vulnerability management and threat assessment solutions, we also offer professional services including penetration testing, social engineering, and PCI compliance scanning and service.
MSPs: Provide dependable, efficient vulnerability management that delivers high performance and high returns
Outsourced cybersecurity is quickly becoming an industry norm. Organizations are looking to Managed Service Providers (MSPs) to provide reliable security solutions that keep pace with growing threats. Protect your clients from vulnerabilities and improve your team's efficiency with Fortra VM, our cloud-native, multi-tenant, SaaS security platform.
Benefits include:
- Rapid monetization and ROI
- Comprehensive support
- Low initial costs
- User-friendly operation

Award Winning
Threat and Vulnerability Management






Start Building Your Vulnerability Management Program
Our experts are here to help you find the solutions or services that fit your organization's security needs.
Let's get started.
Copyright © Fortra, LLC and its group of companies. Fortra™, the Fortra™ logos, and other identified marks are proprietary trademarks of Fortra, LLC. | Privacy Policy | Cookie Policy | Sitemap